ÑÎÂÐÅÌÅÍÍÛÅ ÈÍÔÎÐÌÀÖÈÎÍ-
ÍÛÅ ÒÅÕÍÎËÎÃÈÈ\2.Âû÷èñëèòåëü-
íàÿ òåõíèêà è ïðîãðàììèðîâàíèå
Baizhumanova A.E.
second-year
graduate student
L.N.
Gumilyov Eurasian National University, Republic of Kazakhstan
The circuit work of smart
cards.
Annotation. Information security issues always will be a
priority for a company of any rank, whether it is a private organization or
public institution. Now it is a common practice in large companies to use
two-factor authentication based on smart cards or USB sticks, as a key to
access confidential information. This article discusses the types of smart
cards, structure and functional diagram of a smart card.
Key words: Smart card,
smart card architecture, two-factor authentication, data protection.
Smart
cards - plastic cards with an embedded microchip
(ICC - cards with integrated electronic circuits). In most cases a smart card
contains a microprocessor and an operating system controlling access to the
device and objects within its memory. Additionally, smart cards usually have
the ability to conduct the cryptographic calculations. Smart cards are made of
plastic, generally polyvinyl chloride, but sometimes polyethylene terephthalate
based polyesters, acrylonitrile butadiene styrene or polycarbonate. Since April
2009, a Japanese company has manufactured reusable financial smart cards made
from paper.
The appointment of smart cards - one-and
two-factor user authentication, storage of key information and conducting
cryptographic operations in a trusted environment .
Based on the connection type with the
smart card reader, the smart card can be divided into:
• Contact
Smart Card with ISO 7816 interface;
• Contact
Smart Card with USB-interface;
• Contactless
(RFID) smart cards.
• There are
cards that include both a contact and contactless interfaces.
Based on the functionality the smart card
can be divided into:
• memory card
(contains some data and the mechanism of differentiation of access to them);
• smart card
(contains a microprocessor and has ability to manage data on the card).
let's look at a simplified architecture
of smart card (fig. 1). As you can see here is everything: various types of
memory, the processor and the input output system.
Smart cards are designed to store
information in security; so memory of many smart cards contain additional
elements to ensure data integrity. In addition, in order to complicate copying
of smart card, data stored in its memory is encrypted or written in a
particular order, so reading the sequence of memory cells completely wouldn't
mean reading data sequences. Because of this it is very difficult to analyze
the operation of the smart card by examining the electrical signals in the
crystal or by laminating sawing and analysis using an electron microscope.
Many smart cards have integrated
functions of self-destruction in several unsuccessful attempts to gain access.
For example, we all know after 3 failed attempts to enter your PIN code, your
SIM card will be blocked.
Protection particularly concerns the data
exchange process, because in the process of sending or receiving the data, it
can be listened to or substituted. Relating to this, the work with the card
reader begins only after the mutual authentication with special temporary keys.
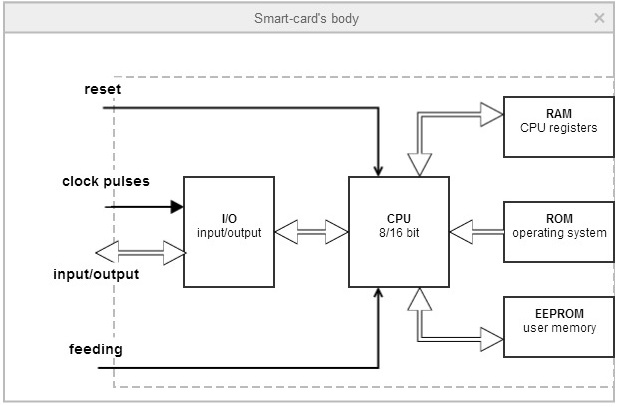
Fig. 1 Architecture of smart card
The same applies to the exchange of
information between the smart card reader and computer. Schematically, this
process might look like this:
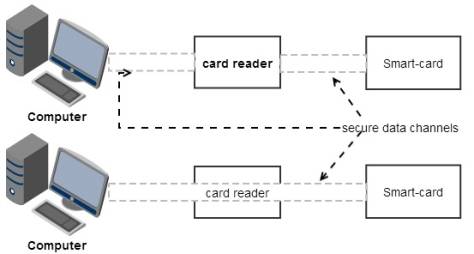
Fig2. Exchange of information between the smart
card reader and computer
The protected work in schemes
"computer-smart card reader- smart card" or direct
"computer-smart card" is possible. By using a computer network the
work with smart cards can be brought to the level of "server-smart
card", in this case all exchanges of information will be protected, no
matter how many intermediate nodes are used.
Let's look at the architecture of the
smart card again. CPU of smart card is one of the main components. It provides
the correct operation throughout the whole card. Bit processor in the cards is
different, today most often 8 or 16 bit.
The number of contacts of the smart card
is limited to 6 or 8 and that’s why information input/output is made with
bit-serial transmission over a single channel. For smart cards requiring high
exchange intensity, for example for memory cards or cryptographic cards,
manufacturers make two-wire or three-wire exchange. In contactless smart cards
input/output device has required in this case, the radio transmitter and
receiver, as well as system providing the smart card with power supply.
The last thing I want to mention is the
physical memory resources. Nothing lasts forever, so writable EEPROM memory has
some limitations, such as the number of overwriting information and the minimum
retention period. I think it is not possible to check the accuracy of all of
these parameters for the common user, however, almost all manufacturers of
smart cards guarantee a minimum number of overwriting about 100,000 times and a
minimum retention period of data up to 10 years. Of course it will depend on
the conditions of the smart card, and may be it will stretch for 10-15 years,
but usually developers consider the average operation life like 3-5 years. Most
often, smart cards have even lower lifetime (from several months to 2 years),
and out of operation without developing a tenth of its potential resource.
So smart card is a device that helps us
store data in protection. The appointment of smart cards - one-and two-factor
user authentication, storage of key information and conducting cryptographic
operations in a trusted environment. Many of today's smart cards have been
certified for compliance with industry and government security standards. Now
we can see that smart card become a worth part of our daily life, and we should
know how it is works in order to improve its protection.
List of references:
1. Brian Komar, “Get
Smart! Boost Your Network's IQ With Smart Cards”, http://technet.microsoft.com/en-us/magazine/2005.01.smartcards.aspx
2. “Types of
Smart Card”, http://www.smartcardbasics.com/smart-card-types.html
3. Jorge
Ferrari, Robert Mackinnon,Susan Poh, Lakshman Yatawara , “Smart Cards: A Case
Study”, 1998, 6 page, 41-43 page.
4. “Ñìàðò
êàðòû. Ñìàðò-òåõíîëîãèè”, http://www.idexpert.ru/technology/122/
5. Àíäðåé
Ìåæóòêîâ, “Áåçîïàñíîñòü ïëàòåæíûõ ñìàðò-êàðò”, http://www.xakep.ru/magazine/xs/061/090/1.asp