ÌÀÒÅÌÀÒÈÊÀ / 5. Ìàòåìàòè÷åñêîå
ìîäåëèðîâàíèå
Ph.D.,
Professor Abdimomynova M., Master IS Doumcharieva Zh., Master INF Aitbaeva
Z.
Taraz State University, Kazakhstan
Computer and Mathematical
modeling of two voice signals
In today's
world, more often interested in speech technologies, in particular, identification
by voice. This is due, on the one hand, the advent of high-performance
computing systems based on personal computers and hardware, allowing to make
the input signal to the computer, and, on the other hand, a high demand
authentication systems in different fields of human activity. This method is
easy to use.
Today is the
time - when developing new technologies. On the streets in the stores set the
camcorder. They allow you to record not only video but also audio. For example:
a person walking down the street talking and the sound of the camcorder is
writing gave him a computer and he analyzed his voice was checked for a match
on the database. When you need to determine the identity of a specific person
voice, the program will compare the spectra of a few words and give the
probability of a match. Precise identification of the person is an important
element in various situations, for example in law, criminology, legal
paperwork, and many other areas.
Study of the problem
analysis of two voice signals can be successfully applied in forensic science,
case management, at security checkpoints to restrict the admission and finding
people for various emergencies such as plane crashes, based on the records of
talks can be restored setting and a picture of the incident, to determine who
speaks a particular phrase. Moreover, the voice may be approximately appearance
(appearance) portrait telephone blackmailers, terrorists and other criminals.
In modern jurisprudence voice can serve as a clear piece of evidence in court.
The aim is to create a program capable to analyze the human voice with a record
from the database.
One of the
challenges in the field of speech technology is to determine which person
corresponds to a particular speech signal. System solves this problem fall into
two broad classes - the system of verification and identification. Verification
- a procedure to confirm the identity of the speaker, and the identification -
determination of the individual from a given, limited list of people.
Currently, the system of identification and verification of voice are becoming
increasingly popular around the world. This is primarily due to natural and
habitual speech interaction between man and computer system.
To analyze
voice signals necessary:
• Get a
voice signal,
• Improve
signal (to remove noise)
• Highlight
words
• Compare
the received signal to the database,
• Find the
percentage of matches.
For voice signal algorithm that allows you to record
sound from a microphone.
To record a sound, first set the buffer size «BufSize:
= TrackBar1.Position * 500 + 100" and then the following parameters
sampling: «wFormatTag: = WAVE_FORMAT_PCM, nChannels: = 1 (1 mono 2 - stereo) -
the number of channels, frequency, equal to 44100 (8000 possible values, 11025.
22050 and 44100). and bit rate equal to 16 bits, leveling blocks «nBlockAlign:
= nChannels * (wBitsPerSample div 8)" The number of bytes per second. For
this is the result WAVE_FORMAT_PCM nSamplesPerSec * nBlockAlign.
Then open the audio device «WaveInOpen (Addr (WaveIn),
WAVE_MAPPER, addr (header), Form1.Handle, 0," set to the length of the
buffer, its name, and load data into it.
Obtained from the microphone signal to be
processed by a Fourier transform obtain spectrum.
The Fourier Transform - a mathematical
process that allows us to take the time (seismic trace) and express it as a
function of frequency (spectrum) of the formula:
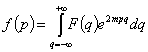 (1)
(1)
But it is quite
complicated and therefore has been used "Fast Fourier Transform".
The resulting range of 4
seconds output using TChart screen.
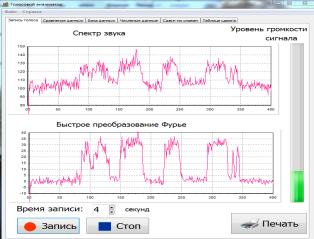
Figure 1. The window program (Voice Recording). Recording from a
microphone and receiving range of sound.
To date, most of the work to clean up the sound is reduced
to getting a sample from the hiss and noise - «hiss," high-frequency
noise. Hiss - even hiss. Noise - a broad term, in fact, the same.
There are two methods of cleaning. The first - the
threshold - noise gate, simply filtering. It frequency filtered out. To begin
with - all of top, which not clogged sound formants, namely noise.
The second method is that the program is scanned
sample of noise, and then the algorithm would be deducted from the noise of the
waves.
I had to use the second type of program.
Further it is necessary to amplify the signal and
remove noise (filter), using the following algorithm:
s:=trunc(s/bit);
s1:=trunk (s1/bit)-20;
if abs(s1)<11 then s1:=0;
ss [i+k]:=s1;
form1.Chart4.Series[ng].Add(s); form1.Chart3.Series[ng].Add(s1);
i:=i+bit ;
Then select from the signal words and working more
with words.
Now we can compare the two voices, a new and already
existing in the database.
Find the differences between the two signals. We
calculate the percentage of matches, as far as one signal coincides with the
other according to the formula:
Ð=![]() (2)
(2)
In the Delphi-voice
analyzer developed algorithm and program in the language of Code Gear Delphi Architect
2009 can record and compare the audio material to the database. It happens that
the anomalous voices defined and recognized relatively easy. In other cases,
the ruggedness and the duality of sound does not allow them to identify
reliably. In such cases, only the computer analysis can give more data than a
regular hearing, unbiased information.
The signal can vary over
a wide range of pure and easily analyzed to noisy and not treatable.
Over time, the study of
the votes based on computer analysis using a variety of methods of analysis of
voice put a solid foundation for accurate identification of people.