Modern information technology/4. Information
Security
Morozova
A.N.
State
higher education institution
"National
Mining University"
Steganography methods for transmission of messages in audiosignal
Methods of steganography got active
development with the advent of computer technology, when it became possible to
use multimedia files as a container for information transfer. Ones of the most
commonly used containers are multimedia files. Investing in multimedia
containers based on the fact that the human senses have certain selectivity,
therefore, to provide a good perception, digital multimedia content has the
property of redundancy. This makes it possible to use the least significant
components of the necessary information required in order to conceal it.
Human
hearing system can be represented as a frequency spectrum analyzer, which can
detect and identify signals in the range of 20 - 20,000 Hz. Human hearing
system can be modelled as 26 band pass filters, which bandwidth increases with
increasing frequency. In connection with this particular development methods
have digital steganography audiosrede. Hiding data in the sound (audio) signals
is particularly promising. Today there are many software products that have
different capabilities, operating principles, scope, format of data used and the
preferred software platform.
Essential
influence on reliability of stegosystem and possibility of detection of the
fact of transfer suppressed messages renders a container choice. For
realization of introduction of additional information it is best of all to use
audio the file in the WAVE format. When we use WAV format it is necessary to
make changes to a sound wave that in very small degree influences sounding, it
very much increases probability to leave the hidden message unnoticed.
There
are various algorithms for data hiding in audio systems. Among them are the
phase coding as one of the most effective ways. The system of the human
distinguishes changes hearing of a signal phase more weakly than amplitude or
frequency changes, such feature of human perception is the reason for the
effectiveness of these algorithms.
Implementation
of phase modification audio information is a method in which the phase of the
initial segment of the audio signal is modified depending on the implemented
data. Phase subsequent segments agreed with it to save the phase difference. It
is necessary because the phase difference to the human ear is more sensitive.
Phase encoding is one of the most effective methods of steganography by the
signal noise is perceived, which allows more seamlessly embed additional
information. Further
two algorithms implements coding with using of modifications of the phase of
the original signal.
Method
based on a phase difference.
Procedure
of phase encoding consists in the following:
1. Sound sequence ![]() converted into a series of N short segments (blocks)
converted into a series of N short segments (blocks) ![]() .
.
2. The N-th segment of
a signal ![]() is applied Ê-point discrete
Fourier transform, where
is applied Ê-point discrete
Fourier transform, where ![]() , and creates arrays phases
, and creates arrays phases ![]() and amplitudes
and amplitudes ![]() for
for ![]() .
.
3. The difference of
phases between each next segments is remembered for ![]() :
:
![]() ;
; ![]() .
.
4. The binary sequence
of data is represented as ![]() or
or ![]() displaying respectively "1" or
"0".
displaying respectively "1" or
"0".![]() .
.
5. Taking into account
a difference of phases the new massif of phases is recreated for ![]() .
.
6. The matrix of
phases is anew created, using the kept difference of phases/
7. Using the new array
of phases and the array of amplitudes, components of a complex range that is
necessary for performance of the return transformation of Fourier are
calculated.
8. Restoration of a
sound signal is carried out by application of operations of the return DPF to
an initial matrix of amplitudes and the modified matrix of phases.
The
relative phase difference between each adjacent segments remains. It is this
relative difference in the phase of the human ear is most sensitive. The
drawback scheme which is based on the method of phase encoding is a low
throughput.
For an
assessment of this method it is necessary to find an assessment of ![]() information message and to
define its error. The idea of the proposed method is based on the determination
of the phase characteristics of the signal received by the Hilbert transform emissions.
Since the analytical solution of the problem is difficult, the proposed
solution is justified by computer simulation. Method for solution of the
problem involves the following operations:
information message and to
define its error. The idea of the proposed method is based on the determination
of the phase characteristics of the signal received by the Hilbert transform emissions.
Since the analytical solution of the problem is difficult, the proposed
solution is justified by computer simulation. Method for solution of the
problem involves the following operations:
1. Formation of the
signal container containing an information message ![]() .
.
2. Definition Hilbert
image of a signal container, where H – the operator of Hilbert transform:
![]()
3. Definition of
fractional part of the phase characteristic of a signal container:
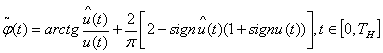
4. Expansion of the
phase characteristic of a signal of u (t) on an interval of its supervision for
the purpose of receiving an assessment of the developed phase characteristic,
where – ![]() the step function determined by jumps
the step function determined by jumps![]() :
:
![]()
5. Assessment of an
information message as differences of the phase characteristic of a signal ![]() and a signal container phase without an
information message:
and a signal container phase without an
information message:
![]()
6. Definition of an error
of an assessment ![]() :
:
![]()
The
offered method of the hidden information transfer is based on use of phase
characteristics of signals. Increase of reserve is reached for the account
modulations of parameters of a signal container on small time intervals,
comparable with its period. Increase of accuracy of measurement of phase
characteristics is reached by a way additional weight processing of a signal
container.
For
increase of efficiency of this algorithm it is recommended to use cryptography
methods for preliminary encoding of the text of the message. Joint application
of algorithms of a steganography and cryptography increases reliability of
transfer of the message.
Analysis
of trends in computer steganography shows that in the next few years, interest
in the development of its methods will grow more and more particular. It is
well known that the problem of information security is constantly growing and
encourages the search for new methods of information protection. This article
has discussed algorithms for hiding information in audio signals based on phase
modification of the original signal. Selection of these methods is caused by
their simplicity and that they allows to hide in rather small files rather
large volumes of information without significant changes in file sounding for
perception the person.
References:
1. Basics
of computer steganography/ VA Khoroshko, A.D. Azarov, J.E. Rustle and others,
Vinnitsa, Vinnitsa state technical University, 2003. - 143 p.
2. Bendat,
J., A. Peirsol Applied analysis of random data: Per. from English. - Academic
Press, 1989.-540 p.
3. W.
Bender, D. Gruhl, N. Morimoto, A. Lu, Techniques for Data Hiding. IBM Systems
Journal, 35(3&4): pp.313-336, 1996.