Engineering science / 12. The
automated control systems on manufacture
Kulyk A.J., Krivogubtchenko S.G., Kulyk J.A.
Vinnitsa national technical university, Ukraine
An information transmission in the conditions of the adaptations
of transmission information system to communication channel parameters
As it has been
shown above, in real conditions information transfers a large role are played protective coding of information.
Volume of final file, and accordingly, and time of transmission essentially
depend both from chosen
algorithm of the coding, and on quantity of errors which must be corrected for every
code combination. During development of transfer protocol arises up exactly problems (to the choice of code algorithm with
determination or
with the correction of errors, and also determination quantity of errors,
which need to be corrected). The
choice of parameters with a supply often results often
results in the uneffective
use of channel. Proceeding
from it is expedient
to develop an algorithm which
would allow correcting
this ambiguity.
The specified problems directly linked from time of
the use of|употребления | information interchange channel. Except speed of
transfer this parameter depends on length of a message of information (to volume of a
file which should be transferred), lengths of the block of details what are transmitted,
and quantities of errors which should be corrected:
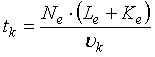 , (1)
, (1)
where tk – time of use of a
communication channel, s;
Le –
length of an elementary message of information, bit;
Ke –
quantity of control categories which are added to an elementary message of
information, bit;
Ne – quantity
of elementary messages which make a transmitted file;
хk – speed of
transmission, bit/s.
The comparative analysis of algorithms of
construction of elementary messages taking into account quantity of control bits is already considered above. For
modern transfer information system, which is built on the base of microprocessor means, the
most widespread formats for protective codings is the byte or half-byte. The quantity of check bits what
are added
to
information, does not depend on algorithm of the coding (Hemming, cyclic etc.), and is defined only by quantity of
errors which should be corrected, and in the length of an elementary message of
information. Thus, the basic problem is the choice most economic algorithm of the
coding by a
communication channel operating time.
The use of microprocessor tools allows to divide the
process of data preparation and process of transfer in time, spending at first the
coding and, in case of need, repacking data, and then them transfer
by a communication
channel. It allows to liberate the channel for a while processed data on the transfer and
reception sides.
If the algorithm of the coding with
correction of errors is not used, and there is enough only their fixing, serial interfaces during data transformation time from a parallel code on successive are
able to add the check bit of odd-even check without implementation of
superfluous operations
during preparation of information. For algorithms of the coding with correction
of errors it is necessary to predict quantity of errors, which can arise up during transfer of elementary message. It can be carried out only after communication channel
testing. In the literature [1] theoretical transfer of information are considered by a communication
channel with hindrances and it is shown, that conditional entropy is:
![]() , (2)
, (2)
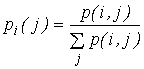 (3)
(3)
Also
characterises the particle symbols, which are distorted hindrances during information
transfer. Proceeding
from it, it is expedient to realise device adaptation |до |to transmission
conditions so that
depending on probability distortion signals and zeros to define quantity of errors, which is necessary to correct in the
elementary message [2, 3, 4, 5].
Thus, stages of information
transfer define sequence of operations:
Ø
on the first testing of
communication channel is carried out for what it transfers sequence of signals and
zeros which is processed on the reception party, where middle probabilities of distortion of signals р1 and zeros р0 are determined, the results of calculations are passed to the transmitter;
Ø
on the second stage the most effective algorithm of
code is determined and preparation of information is carried out to the transfer process which, except for a protective coding, in
the case of necessity contains and transformation of information to elementary message;
Ø
on the third stage the transfer of information
is carried out by a communication channel.
As well as the majority of
microprocessor structures, the information transfer device can be built with use of a mode
of programmatic exchange by information or a mode of interruptions.
Both of them have certain advantages and lacks, but in this case it is
expedient to use the second of them that the personal computer had possibility except
function of information transfer to execute et al.
Process of exchange
information by a
classic structure, resulted
on figure 1, it is expedient to execute in a few stages.
At the first stage
communication channel testing is carried out. Thus the
test sequence of signals and zeros for probability definition hindrances elementary binary signals is sent to a reception side. Signals transform after the proper law of
modulation.
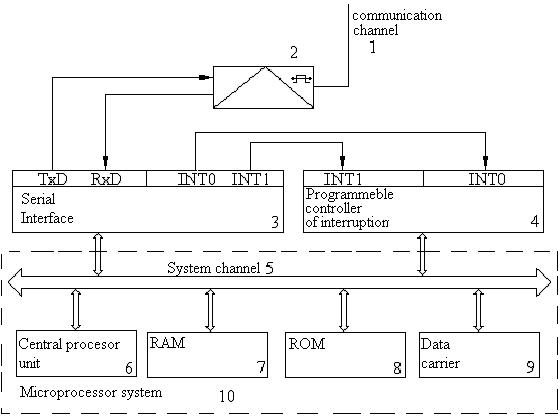
Figure 1. The
generalised structure of realisation of
method of
information transfer with information adaptation
From a reception part the message on quantity of
deformed signals and zeros proceeding from what it is possible to calculate
probabilities of errors in a communication channel for signals р1 and
zeros р0 that should be transferred, behind formulas arrives:
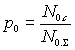 , (4)
, (4)
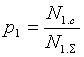 , (5)
, (5)
where N0.c and N1.c –
accordingly quantity of zeros and signals of the test message which have been
deformed by hindrances during information transfer by a communication channel;
N0.In and N1.In –
accordingly quantity of zeros and signals in the test message.
The
error on quantities of the information which is transferred by a communication
channel, is equaled that part of this information, which| is absent in the accepted signal, in other words, that uncertainty in relation of transmitted signal, which takes place when the accepted signal is
known. Actually it will be defined middle entropy:
![]() . (6)
. (6)
Taking into
account principles of formation of data in microprocessor systems, it is
possible to consider them not correlated. Proceeding from the formula (6)
entropy for signals Н1 and
zero Н0 will make:
![]() , (7)
, (7)
![]() . (8)
. (8)
Calculated
to entropy will show the
particle of signals, which can be distorted during an information transfer. For
simplification it is
expedient to choose greater from them, getting a result with a supply|:
![]() . (9)
. (9)
The quantity of elementary signals which can
be distorted
hindrances during a transfer of communication channel, is:
![]() , (10)
, (10)
where n – volume of a file which should be
transferred, byte.
Quantity of
errors, what it is necessary to correct in each message,
is:
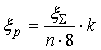 , (11)
, (11)
where k –
quantity of information bits in each message.
Thus,
at the first stage the quantity of
information bits in each message, which can be
distorted, are
determined. For realization of code algorithm this parameter must be rounded off in a
greater side to the integer:
![]() . (12)
. (12)
On the second stage an algorithm
gets out and the code of information is carried out in accordance with the
chosen algorithm. If it is
necessary to correct two
errors, the transmission must be carried
out half-bytes (four informative and nine check bits). If correcting is necessary one error, it is possible to transmit information half-bytes (four information
and three control categories) or bytes (eight information and four control
categories). The type of algorithm of the coding (Hemming, cyclic and so forth) has no principle value. But taking
into account that consecutive interfaces carry out transmission
only eight bits (if digits less than, they are complemented zeros|), for time reduction of information
transfer channel use after protective coding
it is necessary to carry out transformation data, complementing insufficient to eight quantity of digits from a next byte.
At the third stage is carried out transfer of official messages relation algorithm of the coding (type
and quantity of errors which are corrected) by an arbitration method. Thus the same message is transmitted a few times, and on a receiving side on receipt the most credible gets out on bits.
After that, enters to the action the transmission of
basic information.
The test message can be transmitted a few times on different speeds for the purpose of determination such on which distortion will be the least. Transmission
of the results of processing from a receiving side to the transfer is expedient to carry out in the mode a reiteration with the
majority decoding, when
data are transferred odd quantity of times|свершать | and the bit-by-bit comparison of code combinations is make for determination of correct.
If the channel is
symmetric (р1 = р0 = р) calculation
of conditional entropy does not cause the difficulties:
![]() . (13)
. (13)
If the channel is asymmetrical, for
calculation it is necessary to use greater from the got|receive| probabilities. In principle, it is possible
to count up quantity of signals
and zeros in a file
which must be transferred and precisely enough to calculate value of conditional entropy taking into account distortion zeros and signals for an asymmetrical channel. But, except
large complication of calculations, the result will not be reliable as after
carrying out protective coding the quantity of signals and zeros will change. For determination of eventual parameter of recommended approximate calculations it fully sufficiently.
After definition of conditional entropy it
is possible to choose
optimum length of the elementary message and to define the quantity of errors, which can arise after its transmission and which will need to be corrected.
As the communication channel is used during the enough limited time, hindrances in it can be
considered as stationary casual process. Then the estimation of length of test
sequence zeros and signals can be spent
behind a method considered above.
The developed adaptive method allows
to define necessary parameters for protective coding and to optimise information transfer process at the expense of the
proved choice of quantity of errors which should be corrected, and reductions of
time of the use of communication channel.
References.
1.
Шеннон К. Математическая теория связи. // К.
Шеннон Работы по теории информации и кибернетике. – М.:
Иностранная литература, 1963. – с. 243 – 332.
2.
Кветный Р.Н. Применение метода мажоритарного
декодирования в адаптивных системах передачи информации / Р.Н. Кветный, А.Я. Кулик
// Оралдын Fылым Жаршысы. – 2007. – № 7. –
С. 83 – 92.
3.
Кулик А. Алгоритм адаптації до умов передавання інформації каналом
зв’язку / А. Кулик, С. Кривогубченко,
М. Компанець, Д. Кривогубченко // Контроль і управління в складних системах: VI
міжнар. конф. Вінниця, 8 – 12 жовтня 2001 р. – Вінниця: ВДТУ, 2001. – С. 151 –
152.
4.
Квєтний Р.Н. Методи адаптації пристроїв передавання інформації до параметрів
каналу зв’язку: монографія / Р.Н. Квєтний, А.Я. Кулик, С.Г. Кривогубченко, Д.С.
Кривогубченко. – Вінниця: УНІВЕРСУМ-Вінниця, 2005. – 161 с.
5.
Патент 48409А України, МПК7 Н03М 13/00. Спосіб кодування та
передавання дискретної інформації з адаптацією до умов передавання та пристрій
для його здійснення / Квєтний Р.Н., Кулик А.Я., Кривогубченко С.Г. та ін.
(Україна); ВДТУ. – № 2001064411; заявл. 23.06.01, опубл. 15.08.02, Бюл. № 8. –
10 с.