Abstract: This paper explores on the aspect of application of
quantum cryptography in
wireless networks. In
this paper we
present a methodology
for integrating quantum cryptography and security of IEEE 802.11
wireless networks in terms of distribution of the encryption keys. Quantum cryptography provides a solution
towards absolute communication security over the network by encoding
information as polarized photons, which can be sent through the air. Present use NS2 simulation for designing
wireless networks and using
Cryptography algorithm as
to security information.
Key
words: Network Security,
Quantum Cryptography, Wireless Network, IEEE 802.11, Key Distribution.
INTRODUCTION
Wireless networks generate
large amount of
data, which often
is sensitive and
vulnerable to interceptions than
wired networks. This
has increased the
risk for users
significantly and to combat
this consideration, wireless
networks users may
choose to utilize
various encryption
methodologies. Encryption is
the key to
keep information secure
online in a
Wi- Fi network.
When
information is encrypted, it’s scrambled into a code so others can’t get it.
Thus, due to the high probability of information compromise associated with
Wi-Fi networks, various encryption methods have been developed. However,
commonly utilized encryption methods are known to have weaknesses and are
susceptible to attackers thereby compromising confidentiality.
In order
to make secure
communications around a
wireless network, communication between nodes (users) and base station (BS) to other nodes should
be handled carefully by means of an efficient
key management protocol.
Quantum Key Distribution (QKD) using quantum cryptography is a new method in key distribution scheme, which allows
broadcast of a network key with absolute
confidentiality.
Related
Works
Quantum cryptography is
described as a
point- to - point secure key
generation technology that has
emerged in recent
times in providing
absolute security. Researchers
have started studying new innovative
approaches to exploit
the security of
QKD for a
large- scale communication
system. A number of approaches and models for utilization of QKD for secure
communication have been developed. The
uncertainty principle in quantum mechanics created a new paradigm for QKD [1].
One of the approaches for
use of QKD involved network
fashioned security. BBN
DARPA quantum network is an
example of such network.
Researchers at Boston, Harvard
University, and BBN technologies jointly developed the DARPA Quantum
Network in 2004 [2]. The main go al
was point- to - point Quantum network
that exploited QKD
technology for end - to - end network security via high speed QKD.
Wireless Networks
In today’s
era, everyone wants
their necessary data
to be handy, portable and
accessible from almost every
place they visit
throughout the day
and this is
made possible by
using wireless networks.
Wireless networks, as
the name suggests,
are those networks
that are not connected by any physical means such as
Ethernet cables and thus provide the user with great mobility and
convenience. Also, it
saves one from
the expenses on
the cables that
would be required if wired
network is chosen as well as makes it easier for moving the base of the devices
from location to another by just moving the machine along with the wireless
network card.
A
wired network helps
in point to
point transfer, that
is, sends data
between any two
devices that are connected with each other through an Ethernet cable but
in case of wireless networks, the transfer of data is a broadcast service where
the data is sent to all possible directions in the medium within
a limited range
as the medium of data
transfer is air
here and not
cables.
Wireless networks consist
of four basic
components: Transmission of
data using air waves, access points (AP) to establish a connection to the public
or private (organization) network and
the wireless client operated by
the user.
Security Issues in Wireless Networks
Wireless networks do
not promise quality
of service during
transmission and chances
of intrusion into such
networks are very high
since the transmission here takes place
through the medium of air and not cables. So, it doesn’t
only require protection against uninvited users from accessing the network but also needs to secure the users’ private
data that is being transmitted. The
general security issues for wireless networks are as follows [3]:
ü Confidentiality;
ü Integrity;
ü Availability;
ü Eavesdropping and
ü Authentication;
ü Blue Snaring or Blue jacking;
ü War Driver.
Overview of Classical Cryptography
Cryptology is defined
as the practice and study
of techniques for
secure communications in presence
of adversaries (third parties), which underpin cryptography and cryptanalysis.
Cryptography is composed of two major goals:
• Information
privacy: For keeping information
transmitted via a network private without giving any information to a third
party and
•
Authentication: To check the integrity of the message received by the
user from another party connected via the same network.
Data security
depends entirely on
the secrecy of
the key. Classically
cryptography algorithms are
divided into two forms depending on key distribution techniques:
i. Symmetric Key Algorithms - Cryptosystems that make
use of symmetric key distribution use same key
for encryption and decryption. This method is
also known as
secret key cryptography. Secure communication
channel in key management is
achieved only if
the symmetric keys
are pre- distributed in
to every pai r of interactive
systems.
ii. Asymmetric Key Algorithms - Cryptosystems that
make use of
asymmetric key distribution use a public
key system that consists of two parts: a Private key,
which is kept secret and a Public key, which is distributed over the
network. The sender
encrypts the message
using the public
key of the receiver. The receiver makes use of its private key to
decrypt the message. In such a distribution the private key is never in transit
and hence less vulnerable to security issues[4] .
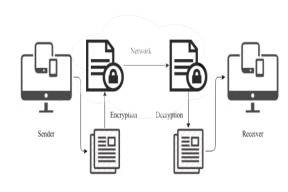
Figure 1. Process of Cryptography
Cryptanalysis on the
other hand refers
to study of
cryptosystems with a
view to finding weaknesses in them that
will permit retrieval
of the original message from
the encrypted message, without
the knowledge of the key or the algorithm used.
Overview of Quantum Cryptography
Quantum cryptography [5] is an evolving
technology that provides
safety and security
for network communication by performing cryptographic tasks using
quantum mechanical effects.
Quantum
Key Distribution (QKD) is a technique that is an application of quantum
cryptography that has gained popularity
recently since it overcomes the flaws of conventional cryptography. QKD makes
the secure distribution of the key
among different parties
possible by using properties of physics.
The quantum
states of photons
are used and
the security key
information is transmitted
via polarized photons that
contain the message
denoted by bits
(0 or 1) and each
photon contains one bit
of quantum information
called as “Qubit”.
The sender sends
the polarized photon
to the receiver. At the receiver
end, the user determines the photon polarization by passing it through a filter
and checks for any modifications in the received bits of photons when compared
to the bits measured by the receiver. Any modifications found would show that
there has been an intrusion from a third
party because the
intrusion would irreversibly change the encoded data in the photon
of either the
sender or the
receiver. This method
is based on
the Heisenberg’s uncertainty
principle that states that the quantum state can’t be measured without
disturbing the state of
either the sender
or the receiver and hence
introducing an anomaly
in the quantum system that can
be noticed by users as an intrusion.
Thus,
Quantum cryptography applies the principles of physics governed by the laws of
quantum mechanics for distributing the secret cryptographic key among the
parties involved in
the cryptosystem in a manner that makes it next to impossible for a
third party to eavesdrop.
BB84 QKD Protocol
I n order
to facilitate QKD many protocols exist such as: BB84 [6], B92, Six - State,
SARG04 [7], Ekert91. Among these
protocols, BB84 is
the most popular
and widely used
protocol for key distribution in practical systems .
Bennett and
Brassard proposed BB84
protocol in 1984.
The protocol consists
of two main channels used for transmission:
1) Quantum channel: One- Way communication.
2) Classical channel: Two- way communication.
BB84 allows
two parties conventionally a Sender and a Receiver to establish communication
by a common key sequence using polarized photons. Key exchange and key sifting
are done as follows.
Using Classical channel (Key Sifting):
•
Receiver informs the
Sender what bases
he used to
measure the photons
and Sender
responds by saying if it matched the bases used.
• Both agree
on to the correct matching of
the bases used
and without announcing
the actual value of information. After discarding all the data on the polarizer
bases that did not match, both
are left with
two key strings
of shorter sequences,
known as the
raw keys.
IEEE 802.11 WLANs
The main
objective of this paper is to offer secure key distribution in wireless
networks making use of Quantum
Cryptography. In order to properly
facilitate the functioning of QKD it is found that IEEE 802.11 family best
suits to be integrated with QKD. Fig.
8. Shows the architecture of IEEE 802.11.
Some of
the characteristic s of
802.11 WLANs that
give it the
proper environment for incorporating QKD are as follows:
1)
Usage: 802.11 WLANs
are mainly used
in office and
campus infrastructure, which facilitates the deployment of QKD
network with a high density of quantum apparatus if necessary.
2) Capacity:
Terminals present in a 802.11 WLAN have more computational capacity and more
energy as compared to those in cellular networks.
3)
Connection: 802.11 WLANs
are used to
provide access to
the Internet through
an AP installed in an
organization, which is beneficial for QKD integration.
In order
to facilitate efficient authentication and management of keys between access
point and client, along with
user traffic control
802.11 networks employs
Extensible Authentication
Protocol (EAP) [8] .
EAP provides an
authentication framework, which
will be used
in the current work.
The security of
802.11 WLANs is
based on the
WEP protocol, with
enhanced security being provided by the MAC layer. As specified earlier
WEP presents security problems in
a wireless network.
4 -Way Handshaking
The 4- Way
handshake performs the
authentication process in
IEEE 802.11 networks.
The process allows the AP and the BS to generate the key hierarchy in
order to provide encryption for
secure communication. Since
the keys are
generated using a
pseudorandom function, in order
to further randomize
data two random
nonce values are
transmitted between the
AP (ANonce) and BS (SNonce).
4 - way
handshake itself has some flaws that inhibit secure communication in a network.
Some of the vulnerabilities are
[9]:
1)
Security Attacks: Vulnerable
to attacks like
DoS in which intruders can
torrent message to the BS after the handshake is completed.
2)
Response Time: BS
will disassociate and
de-authenticate AP if
data flow not received within the expected time
interval after a successful handshake.
3) Air cracking:
Keys can be
recovered using this
program once enough
data packets have been
captured.
In order
to overcome these weaknesses we propose an integration of quantum cryptography
in this key distribution mechanism as presented in the following
subsection.
Wireless
Network Based On NS2
Design of
wireless Network uses NS2, as a base on Security evaluation, and describes the
proposed model of the system and
complete description of
the Simulations and
software program needed for
implementing the Network.
Ns-2 is a widely
used tool to simulate
of networks.
NS2
(Network Simulator version2): NS2 is a discrete event simulator targeted
at networking research.
It provides support for
simulation of TCP,
routing, and multicast protocols over
all networks wireless.NS2 can be employed in
most UNIX systems and
windows (XP, VESTA and 7). Most
procedure processes of the NS2
code are written in C++.
It uses TCL as
its scripting language,
OTcl adds object orientation to TCL.NS
(version 2) is
an object oriented,
discrete event driven network simulator that is freely distributed
and open source.
Program language in NS2
The reason
for having two programming languages from the aims to
have an easy
to use, yet
fast and powerful simulator. C++ forms an efficient
class hierarchy core of ns-2 that takes
care of handling
packets, headers and algorithms. Object Tcl, or
OTcl, is also
an object oriented programming
language utilized in ns-2 for network scenario creation, allowing
fast modifications to
scenario scripts.
OTcl and
C++ interact with
each other through Tcl/C++interface called Tcl/C++ as
depicted in figure 2:
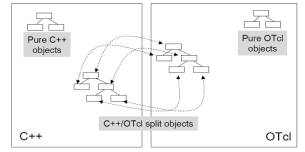
Figure 2. C++
and OTcl Communication
OTcl in
ns-2 enables full
control over simulation
setup, configuration, and occasional
actions (e.g. creating
newTCP flows). It is a language that compromise between speed and
abstraction level offered
to the user[10].
RC5
Algorithm
To design wireless network
using RC5 algorithm to
security of information, RC5
algorithm was developed by Ronald Rivest in 1995 as a parameterized
symmetric encryption. RC stands
for "Rivest Cipher", or alternatively,
"Ron's Code". RC5
parameters are: a variable block
size (w), a
variable number of
rounds (r), and
a variable key size
(k).Allowable choices for
the block size (w) are
32, 64 and 128 bits.
The number of rounds
range from 0 to
255 bits, and the key size
range from 0 to
2040 bits in size.
RC5 has three
modules: key-expansion,
encryption and decryption
units.
Data-dependent rotation (RC5
incorporates rotations) whose
amount is data
dependent. The RC5 algorithm is
designed to have the following objectives:
(a). Symmetric block cipher.
(b). Suitable for hardware and software.
(c). Fast (RC5 is simple algorithm and is word
oriented, the basic operations work on full words of data at a time).
(d). Variable –length cryptography key(k) (0
-2040)bits.
(e). Adaptable to processors of different word-length.
(f). Variable
number of rounds(r)(0-255).
(g). Simple (RC5 simple structure is easy to implement
and eases the task of determine the strength of the algorithm.
(h). High Security (It should provide high security
when suitable parameter values are chosen).
(i). Low memory requirement’s(This property makes the
algorithm suitable for smart cards and other devices with restricted memory).
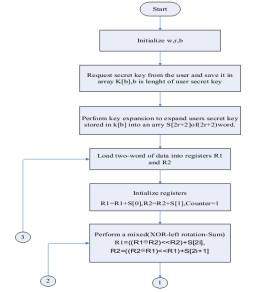
Figure 3.: RC5 algorithm encryption
Simulation Scenario
Wireless network performance
depends mainly on the
end to end. This presented simulation scenario aimed at
activating the network security through network throughput, packet transfer
between nodes within the
scenario by using cryptography algorithms; Simulator RC5 algorithm to
cipher package information that
transfer between nodes[11] .
Simulation principles and strategies adopting the separated object
model and using two
languages C++ and
tclNS2 fulfills the achievement of simulation for
specific protocols and the
configuration nodes and
establishment of network
simulation environment respectively.
figure 4 nam output showing nodes of wireless
networks, Figure 5
refer to drop
of packages when simulation
finished.
Figure 4.Nam output –
Transmission
Figure
5. packets are dropped security packets
(two Scenario)
CONCLUSION
The main
goal of this
research work is
to show a
method to improve
the security aspect of WLANs. It has been
shown that the
integration of Quantum
Cryptography in Wireless Networks has great prospective in
terms of better network security.
Key management
and distribution is
difficult using classical
cryptographic algorithms but
the proposed approach provides a better solution for this problem.
Research has shown that use of QKD
to distribute network
key raises the
security and makes
it harder for
an eavesdropper to interrupt communication. With the
proposed modification, this
paper has achieved
the main objective of improving
security of WLANs.
In this
paper, the software
tool Network Simulator (Version 2), widely known as ns-2,
is described and used for the simulation
of selected illustrative examples of wireless
networks. In general, ns2 provides
users with a
way of specifying network protocols and simulating their behavior. The result
of the simulation are
transfer information secure between nodes.
REFERENCES: