Smagulova K.K.
Karaganda state technical
university
Development of control
algorithm of protection devices against leakage currents, using fuzzy logic
Power
Abstract:
To ensure safe operation of electrical networks with isolated neutral
and electrical equipment in the mining industry devices to protect against
leakage currents are widely used. The importance of such protective devices
demands stringent requirements for their reliability, stability, and the
accuracy of the control parameters of the isolated network. In order to improve
such devices, we offer a method of fuzzy modeling, one of the most interesting
and promising areas of modern high technology. The control algorithm of the
protection device, developed using fuzzy logic, allows the protection device to
fine-tune its control setpoints according to the changing parameters of the
network.
Key words:
fuzzy, logic, leakage, currents, adaptive
1. Introduction
Owing
to the complexity of the physical
phenomena connected with leakage currents,
existing devices developed to protect against leakage currents are inefficient
(Fedorashko, 2004). Existing devices do
not carry out automatic fine-tuning of operation setpoints according to tension fluctuations in the controllable network
nor according to single-phase and diphasic short circuits, both of which lead to increases in
the maximum admissible long current. Further, in underground electrical supply networks, lengths
of protected lines periodically change: such uncontrollable changes of parameters lead to decreases in efficiency of leakage
current protection devices (Tsapenko & Shkundin, 2006). Ideally, a
protection device should possess adaptive properties
which allow it to change according to a network’s
characteristics. We have developed an algorithm to control such an
adaptive system of protection against leakage
currents, using fuzzy logic. In the field of control of technical-systems control, fuzzy logic leads to more effective results than the use of traditional
analytical methods.
Our control algorithm will provide a protection device with the aforementioned
adaptive properties. In the near future we hope to use our control algorithm to
build such a device based on the fuzzy controller.
2. DEVELOPMENT
OF CONTROL ALGORITHM
In order to develop the algorithm, we created a model of an isolated neutral network, using Matlab 7.01,
shown in Figure 1, to
measure the proceedings of such a network and obtain necessary data (Smagulova, 2006).
In our model, scheme 3V was used as the sensor for
the device to protect against leakage currents. The scheme 3V,
consisting of a system of three valves, rectified the operative currents of the network’s circuit (Smagulova, 2007).
From oscillograms recorded during experiments, we identified the
basic features of single-phase
and diphasic short circuits, as well as tension
fluctuations in the network.
Using a fuzzy logic method, preliminary analysis was made to determine input variables for the algorithm (Leonenkov, 2005).
The input variable «voltage signal», being a product of a
fuzzy logic inference, is as a result offered. The given variable denotes the existence and
quantity of phases of short circuits.
According
to order of procedures of a a fuzzy logic inference, the algorithm of Mamdani
makes the fuzzy knowledge base
which are a basis of algorithm of control.
To form rules for fuzzy logic inference
systems, it is necessary to define
preliminary input and target linguistic
variables.
It is evident that for one of the linguistic input variables it is necessary to use the amplitude of tension output from the scheme 3V - «voltage amplitude», and as the second linguistic input variable - «a voltage
signal».
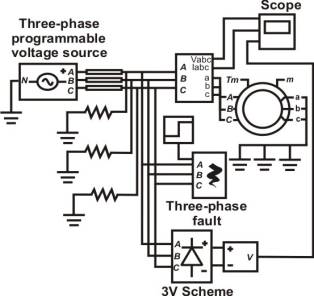
Fig. 1. Model of an isolated
neutral network
As
a linguistic output variable we will use setpoint device operations: g - «setpoint response».
In
this case the system will contain 15 rules
of fuzzy logic inference, as follows:
Rule_1: If ![]() there is a PB PB and
there is a PB PB and ![]() is NS then g PB;
is NS then g PB;
Rule _2: If ![]() there is a PB and
there is a PB and
![]() is ZE then g PB;
is ZE then g PB;
Rule _3: If ![]() there is a PB and
there is a PB and ![]() is PS then g PB;
is PS then g PB;
Rule _4: If ![]() there is a PB PS
and
there is a PB PS
and ![]() is NS then g
PS;
is NS then g
PS;
Rule _5: If ![]() there is a PB PS
and
there is a PB PS
and ![]() is ZE then g PS;
is ZE then g PS;
Rule _6: If ![]() there is a PB PS
and
there is a PB PS
and ![]() is PS then g PB;
is PS then g PB;
Rule _7: If there is ZE and ![]() is NS then g ZE;
is NS then g ZE;
Rule _8: If ![]() there is ZE
and
there is ZE
and ![]() is ZE then g ZE;
is ZE then g ZE;
Rule _9: If ![]() there is ZE
and
there is ZE
and ![]() is PS then g PB;
is PS then g PB;
Rule _10: If ![]() there is NS
and
there is NS
and ![]() is NS then g NS;
is NS then g NS;
Rule _11: If ![]() there is NS
and
there is NS
and ![]() is ZE then g NS;
is ZE then g NS;
Rule _12: If ![]() there is NS
and
there is NS
and ![]() is PS then g PB;
is PS then g PB;
Rule _13: If ![]() there is NB
and
there is NB
and ![]() is NS then g NB;
is NS then g NB;
Rule _14: If ![]() there is NB
and
there is NB
and ![]() is ZE then g NB;
is ZE then g NB;
Rule _15: If ![]() there is NB
and
there is NB
and ![]() is PS then g PB;
is PS then g PB;
Where
NB (negative big) -
the greatest negative
absolute value;
NS
(negative small) - smallest negative absolute value;
ZE
(approximately zero) - closest to
zero;
PS
(positive small) - smallest positive
value;
PB
(Positive Big) - greatest positive value.
The next step of modeling is fuzzification of input variables, a
procedure used to obtain fuzzy meanings (Leonenkov, 2005).
As a term set of the first input variable we will use the
term set = {NS, ZE, PS} with the membership function shown in Figure 2. As a
term set of the second input variable we will use the
term set = {NB, NS, ZE, PS, PB} with the membership function shown in Figure 3. As a
term set of the output variable we will use the term set = {NB, NS, ZE, PS, PB} with the membership function shown in Figure 4.
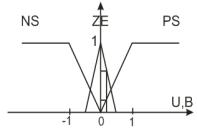
Fig. 2. The membership function «voltage
signal»
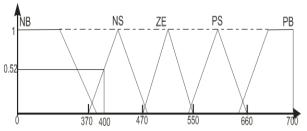
Fig. 3. The membership function «amplitude of the voltage»
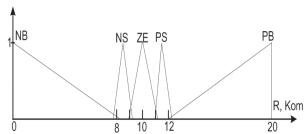
Fig. 4. The membership function «set-point operation»
Using a Mamdani inference algorithm, consider the example, the case when
the protection device’s operation setpoint is 10.0 K Om, current amplitude of
the voltage output of the scheme 3V is 400V and the voltage signal is 0. In
this case, fuzzification of the first input variable (current amplitude) leads
to the term NS (having degree of membership 0.52), fuzzification of the second
input variable (voltage signal) leads to the term ZE (having degree of
membership 1). Thus the conditions correspond to fuzzy conclusion rule number
11. This rule is active and is used in the current process of fuzzy inference.
Aggregation of rule number 11 using fuzzy conjunction operation (1)
results in 0.52.
![]() (1)
(1)
The next step of fuzzy inference is activation of conclusions in the
fuzzy rules. Because weighting factor of all rules equals 1, activation of rule
number 11 results in one fuzzy set.
Accumulation of the conclusions of fuzzy rules using the disjunction
operation to maximize value for rule 11, resulting in a fuzzy set, gives the
membership functions depicted in Figure 5.
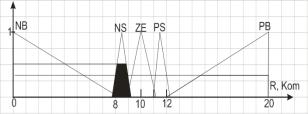
Fig. 5. Schedule of membership functions of two sets of fuzzy linguistic
variables «set-point operation» after accumulation
Defuzzification of linguistic output variables by the centre of area
method for the values of membership functions, shown in Figure 5, leads to a
control variable which adjusts the operation setpoint to K Om 8.5 (approximate
value). Because our second input variable was 0, we know that this value is
proportional to fluctuation of tension in the network of 15% lower than the
nominal value (by the difference 10-8.5).
3. Conclusion
An algorithm providing automatic adjustment
of the operation setpoint of leakage current protection devices, according
to 1) tension fluctuations in isolated
neutral networks and 2) the existence of single-phase
and diphasic short circuits, is thus developed. Application of the given control algorithm in leakage current
protection devices will increase
the performance of such devices, greatly decreasing the number of unnecessary system
shut-downs, while simultaneously better preventing the occurrence of leakage
currents.
4.
References
1. Fedorashko, U. (2004). The
generalized analysis of the touch currents in an isolated neutral network,
according to leakage to the ground. Proceedings
of University, No. 1, (2004), pp 58-59, ISSN 1609-1825
2. Leonenkov, A. (2005). Fuzzy modeling using are Matlab and
Fuzzytech environments, BHV – St. Petersburg, ISBN 5-94157-087-2, St –
Petersburg
3. Smagulova, K. (2007). Development
of protection device against leakage currents in a constant current network, Proceedings of the International scientific
symposium “Modern problems of multilevel education”, Balakiryov, V. (Ed),
pp 74-75, ISBN - 978-5-7890-0438-8, Rostov, 2007, DSTU publishing, Rostov
4. Smagulova, K. (2006). The
modeling of leakage control scheme in a constant current network. Automation and Computer
Science, No 1-2, (2006), pp
10-13, ISSN 1560-7305
5. Tsapenko, E. & Shkundin, S.
(2006). The electric safety in the mining
industry. MSMU
publishing, ISBN 5-7418-0057-9, Moscow