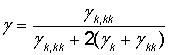St. Petersburg State University of Aerospace Instrumentation
CLASSIFICATION SUBSYSTEM OF INFORMATION SECURITY WITH
MANDATORY ACCESS CONTROL
Abstract. The paper considers a hierarchical structure,
mathematical models and computing procedures of security objects classification
of mandatory access differentiation to informational resources. It allows
shaping tree-type structure of minimally bounding clusters of informational
requests of users with subject to information confidence. The efficiency of the
proposed subsystem is demonstrated on the example of the multilevel
delimitation access to thematic information resources in the satellite information-telecommunication
system in the Republic of Kazakhstan.
Key words: Classification, mandatory access control,
immunocomputing and PCA, confidence,
multilevel delimitation access
1 Introduction
Politics of Information Security of information systems with
confidential information has been settled on the mandate access control. It is
contained in demarcation of rights of access subjects to objects on the base
official permission for reference to the information of appropriate level confidentiality [1].
Mandatory
access control is consisted in the differentiation of access rights subjects to
objects based on the formal authorization (right of access) of subjects to
access information of such confidentiality level. Mandatory access control
includes mechanisms of access differentiation to information. These mechanisms
are divided into procedures realizing the rules of access to information
(reading, writing, addition, etc.), and the procedures for the management
rights (ownership, create, delete, etc.).
As it
is known, significant numbers of models for ensure the security of information
resources has been developed. The most common models are:
·
discretionary access control based on the rules which is defined by
specific discretionary model [2]. For the forming of the access matrix can be
used of Harrison, Rizzo and Ullman models or Take Grant model;
·
mandatory access control [2]. It classical model of the Bell-LaPadula
formally written in terms of the theory of relations. The orderliness between
subjects and objects is taken into account in accordance with their level of
security. The system status varies according to their transformation rules.
However,
despite all the advantages of the Bell-LaPadula model, with its use raises a number
of technical difficulties. This a definition of remote reading status, the
definition of access rights authorized object of type
"administrator"; unauthorized "declassification" of a
object protection with a decrease in the degree of secrecy of information, etc.
For
efficient and secure access to information resources has developed the system
of mandatory differentiation access to information [3, 4] with the maintenance
of its database of multilevel security [5]. Full specifications of subjects and
objects of protection and access rules are stored in this database. This system
contains the following subsystems: mandate access differentiation to
information which has realized as processing database queries monitor; intelligent information security monitoring
with mandate access control [6]. The subsystem provides multilevel protection
against unauthorized access based on the following access rule:
• the subject is not allowed
to receive or record information from the subject or object with a higher level
of protection;
• the subject is not allowed to receive information from an object that
has no access right for current inquiry.
The
main elements of the mathematical model ![]() are: subjects
set
are: subjects
set ![]() ; objects set
; objects set ![]() ; security clearances set
; security clearances set ![]() ; set of access aspects
and control them
; set of access aspects
and control them ![]() ; access rights matrix
; access rights matrix ![]() ; list of current access
; list of current access ![]() ; list of queries
; list of queries ![]() .
.
The
object holder – is subject which it has originated. He can pass to other
subjects the rights on this object access. Using this holder concept each
object is associated with holder (unique user), having the access control
authority to the object. The holder fully controls of producing object and
can’t pass the control authority to other subject. But he may vary the access
control allowing to let or interdict the access other subjects. Such policy
responds to multilevel access control requirements and security system
administrator affects it.
The referencing process to access rights matrix
![]() as to the core
of multilevel security system is jointed with execution such procedures:
as to the core
of multilevel security system is jointed with execution such procedures:
·
definition of conditions and access types to the data of different
security degree;
·
definition of control rights of access law;
·
analysis of filling matrix ![]() with
accounting of execution the main access rule;
with
accounting of execution the main access rule;
·
implementation of domain and creation rights according hierarchy of
security subjects and objects;
·
control of execution the present-day query according the main access rule;
·
safeguard of matrix ![]() from the
efforts of unauthorized modification.
from the
efforts of unauthorized modification.
Intelligent
information security monitoring subsystem has been intended for decision the
next tasks: authentication of security subjects; classification and clustering
of the security objects; analysis of the properties
of demarcation of access rights matrix.
It contains the next modules: learning and self-learning, pattern recognition,
generation risk index, interpretation of the results. Mathematical models and
calculation procedures of Immunocomputing and PCA have been realized in the
above-listed modules [6, 7, 8].
This system has been constructed so that no one user
received the possibility to refer to the information initially belonging to the
owner with higher security clearance during all time of its operation. If there
is the effort of unauthorized access to informational resource it responses on
unauthorized users, violation of the main access rules and conditions of check
access.
Development of methodology for the formation and correct classification
of a protection objects in the system with the mandatory differentiation access
to information of varying degrees of confidentiality allows, first, to fully
implement the analysis of the model in access control for correctness and
completeness, secondly, to realize a complete multilevel security system.
Object access for operating systems was suggested with the positions of
mandatory differentiation access [1, 2], for modern RDBMS [9]. The systems with mandatory policy of information
security were developed [10, 11]. They allowed
realizing the mandate access engine with three-level hierarchy of access
object: data base, table in the data base, data record in table. In the both
cases access objects was invested with only one qualitative index–
confidentiality degree. The approach of step-by-step classification
informational matter was suggested for construction of the object access tree.
Their hierarchy levels reflect the interrelation security subject having the
status of objects security owners.
Tree structure representation of security objects is implemented through
a hierarchy of possession rights of subjects by objects. The hierarchical
dependence between security objects is manifested through the hierarchy of security
degrees of information and through the hierarchy of the classification of
subjects to object. Trunk of a tree of objects is building on degrees access to
information of entities that own objects. The connections between objects are
defined depending on the secrecy of information. The ramification of solutions
occurs through the creation of new facilities owners as a result “the creation
of the sons” of the object.
On each tree hierarchy level there is a need to classifying the security
objects in detail on the following four categories:
-
security degree information which contains or passes in
the security object;
- presentation information type attached to a storage
in the data base or announcements transfer on communications channels;
- coincidence call indicator to the information
by way of active or inactive component of the security system;
- status of information presentation in the security
object.
When
forming a hierarchical set of objects security was used the methods of
clustering information. This made it possible to pick out all the security
objects by executing of proposed procedures of classification. The authorized
access to which ensures the required class of informational security in
computing system and gratification of non redundancy of meta specifications and
non contradictoriness of information resources.
Analysis
procedure of informational matters, a deselect access objects and subjects and
their classification enables the following stages (Figure 1):
-
generation of the security access requirements to informational resources of
different degree confidentiality;
-
execution of computational classification procedures of informational users
queries taking into account informational commonality; degree confidentiality
and clustering index;
- generation of
metadata base of security specifications and database of the multilevel security.
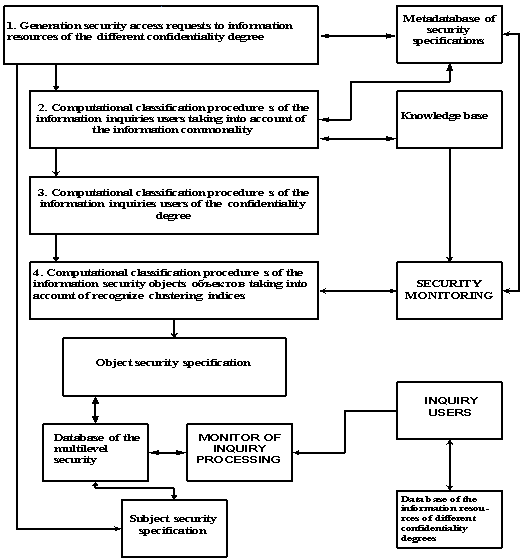
Fig. 1. Hierarchical classification procedures
structure of the information security objects
The mathematical apparatus of the implementation of each listed
procedures will be examined.
2. Mathematical models and
computational classification procedures of the informational queries of the users
The strategy of information protection is created based on an analysis
of requirements to ensure privacy of data domain users, their credentials,
information about the types of data sets and procedures for processing. It
represents a means of establishing the eligibility of each user action with
respect to all types groups of data.
Mathematical model of enterprise is interpreted as:
|
|
(1) |
where ![]() ‑
functions set, are subject to the automation;
‑
functions set, are subject to the automation; ![]() ‑ set of manipulation
data tasks;
‑ set of manipulation
data tasks; ![]() ‑
database users set;
‑
database users set; ![]() ‑ automation
and control objects set;
‑ automation
and control objects set; ![]() ‑ input data of
manipulation data tasks set;
‑ input data of
manipulation data tasks set; ![]() ‑ output data
of manipulation data tasks set;
‑ output data
of manipulation data tasks set; ![]()
![]()
![]() ‑ all
informational items of the enterprise set (exhaustive set);
‑ all
informational items of the enterprise set (exhaustive set); ![]() ‑ relations
between the enterprise components set.
‑ relations
between the enterprise components set.
Formed
requirements of secure access to information of varying degrees of
confidentiality allow presenting a mathematical model of multilevel governance
and access control in the form:
|
|
(2) |
where collections
sets: ![]() ‑
security subjects;
‑
security subjects; ![]() ‑
security objects; JZ ‑ security clearances;
‑
security objects; JZ ‑ security clearances; ![]() ‑ sorts of the access and control them; M ‑ authorization
matrix;
‑ sorts of the access and control them; M ‑ authorization
matrix; ![]() ‑
queries list.
‑
queries list.
For
assurance of separated interface between the different categories of users and
realization of rules and conditions for multilevel security it is necessary to
define the hierarchical dependence inside the set of subjects and objects of
protection subject to the various types of information processing and storage,
of remote and local queries, and the specific subject area, which is
characterized by sets of degrees of secrecy, security clearance, etc.
The
hierarchical relations in the interior of subject sets and security objects
will be defined for different types of information processing and with subject
to distant and local inquiries.
Below
the procedure of construction of stem tree for the security objects is
presented Let ![]() ,
, ![]() è
è ![]() ,
, ![]() ‑ accordingly, set of all
structural elements of the enterprise and set of structural informational
element (IE), subject to security. Information request
‑ accordingly, set of all
structural elements of the enterprise and set of structural informational
element (IE), subject to security. Information request ![]() user
user ![]() (
(![]() ) presents the collection of structured elements EP
) presents the collection of structured elements EP ![]() , moreover
, moreover ![]() ‑ set of all informational requests (IR) of the users with
different access types to informational resources data base (DB). For every
structured element EP user is determined security
‑ set of all informational requests (IR) of the users with
different access types to informational resources data base (DB). For every
structured element EP user is determined security
degree ![]() , where
, where ![]() ‑ the set of security degrees of informational security BD. The
security degree (confidence) is installed by the person, responsible for
security data on the base of the importance degree analysis. For each users
‑ the set of security degrees of informational security BD. The
security degree (confidence) is installed by the person, responsible for
security data on the base of the importance degree analysis. For each users ![]() on
each request
on
each request ![]() is indicated
is indicated ![]() for structural elements and is fixed in
for structural elements and is fixed in ![]() . The authority level of BD user is maximal security
level of the informational BD resource, to which user is letted the access.
. The authority level of BD user is maximal security
level of the informational BD resource, to which user is letted the access. ![]() ‑ set of
the authority levels of BD users.
‑ set of
the authority levels of BD users.
For certain ![]() user
obtains
user
obtains
![]() , where
, where ![]() forms section of the user
forms section of the user ![]() and is
logged â in the authority matrix
and is
logged â in the authority matrix ![]() for
each user
for
each user ![]() .
. ![]() ‑ set, presenting EP for
‑ set, presenting EP for ![]() user;
user; ![]() ‑ informational structural
items quantity in the set. The community analysis establishes on the estimation
of the similarity functions EP. If
‑ informational structural
items quantity in the set. The community analysis establishes on the estimation
of the similarity functions EP. If ![]() ‑ II set of EP
‑ II set of EP ![]() user, then
user, then ![]() will be exhaustive set of II all
users, forming by the way combination II each
will be exhaustive set of II all
users, forming by the way combination II each ![]() , minus recurring elements. Let
, minus recurring elements. Let ![]() ,
, ![]() ‑ unified set of the
informational elements. It includes all sets
‑ unified set of the
informational elements. It includes all sets ![]() ,
, 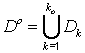 . Let set
. Let set ![]() . If the set
. If the set ![]() is non empty, à intersection capacity satisfies given (threshold)
size and then EP
is non empty, à intersection capacity satisfies given (threshold)
size and then EP ![]() user has sufficient community
degree with the EP remaining users [5, 12]. It allows ganging II of users EP in
one cluster. Similarity measure is calculated as normalized
similarity factor:
user has sufficient community
degree with the EP remaining users [5, 12]. It allows ganging II of users EP in
one cluster. Similarity measure is calculated as normalized
similarity factor:
|
|
(3) |
where ![]() ‑ common elements quantity in
‑ common elements quantity in ![]() è
è ![]() ;
; ![]() ‑ present elements quantity in
‑ present elements quantity in ![]() , but missing in
, but missing in ![]() ;
; ![]() ‑ present elements quantity in
‑ present elements quantity in ![]() , but missing in
, but missing in![]() .
.
The
threshold level of the informational community between EP’s users ![]() is picked from the interval 0,1
is picked from the interval 0,1![]() 0,9. Here it is kept in mind of the informational changing specific
character and type control system. Then the informational compositions of EP’s
users, satisfying the proportion
0,9. Here it is kept in mind of the informational changing specific
character and type control system. Then the informational compositions of EP’s
users, satisfying the proportion ![]() , is taken to alone class, which is maximum bound of the informational
community users class. The hold and processing of collective informational
resources is rationally for this class. If not then users is taken to the loosely
bound class. It is necessary the designing of separated files for this class.
, is taken to alone class, which is maximum bound of the informational
community users class. The hold and processing of collective informational
resources is rationally for this class. If not then users is taken to the loosely
bound class. It is necessary the designing of separated files for this class.
The
clusters forming, minimally and maximum bounding between itself is starting
from a selection in pairs collation sets of the different users informational
elements. The community degrees ![]() set
set ![]() and all remaining sets
and all remaining sets ![]() calculate (here
calculate (here ![]() ‑ the first set number,
‑ the first set number, ![]() ‑ the second set number in
the pair of collation sets), and pick the maximum:
‑ the second set number in
the pair of collation sets), and pick the maximum: ![]() . If
. If ![]() , then sets
, then sets ![]() and
and ![]() is ganged:
is ganged: 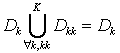 , forming a new set INT(tt) with a concatenated data
set,
where tt – integrated cluster number.
For users requests
, forming a new set INT(tt) with a concatenated data
set,
where tt – integrated cluster number.
For users requests ![]() structured II are organized in LOK(t), where t – local cluster number. The integrated immunity indexes are
calculated in the local and integrated clusters:
structured II are organized in LOK(t), where t – local cluster number. The integrated immunity indexes are
calculated in the local and integrated clusters:
![]()
![]()
![]() .
.
Authority
matrix ![]() is analyzed for each
cluster for the purpose of the isolation of clustered elements
is analyzed for each
cluster for the purpose of the isolation of clustered elements ![]() . These elements generate tree shaft of the security objects.
The hierarchy is rated according access degrees of users
. These elements generate tree shaft of the security objects.
The hierarchy is rated according access degrees of users ![]() to
information
to
information ![]() .
.
These
procedures allow shaping the hierarchical structure clusters minimally bounding
among it with accounting confidence information. As a result the clusters shape
the tree shaft of the security objects.
The
efficiency of the proposed subsystem is demonstrated on the example of the
multilevel delimitation access to thematic information resources in the
satellite information-telecommunication system in the Republic of Kazakhstan.
3. Classification problem on
the set of informational security objects in the corporative net of cosmic
infrastructure
The discipline of informational security of the corporative net
of cosmic infrastructure provides the information
security by means of instantiation multilevel access control to BD,
cryptographic protection of confidential information, verification integrity
transmitted traffics and the assurance of authorization users [13, 15]. The thematic informational outputs are storing,
keeping and handing to the interested organizations.
Below the solution of classification problem is demonstrated on the example
of EP fragment «Remote sensing». It intends for
the control of access differentiation system in corporative net of cosmic infrastructure.
The analysis of objective realm for 6 users was
allowed to isolate 11 typical II (Table 1) – set ![]() è 44 informational structured elements (IE) (Table 2) – set
è 44 informational structured elements (IE) (Table 2) – set ![]() . Initial data and compositions of each informational requirement
. Initial data and compositions of each informational requirement ![]() in the formal
aspect are shown on diagram 1 (Figure 2).
in the formal
aspect are shown on diagram 1 (Figure 2).
Analyses
task of the informational community of isolated requests is solving at ![]() and is receiving four clusters (Diagram 2):
and is receiving four clusters (Diagram 2):
Cluster1=LOK(1)= «P5»; Cluster2=LOK(2)= «P8»;
Cluster3= INT(1) =«P1, P7, P9, P10, P11, P6»; Cluster4=INT(2)=« P2, P3, P4».
Table 1. List of informational previewing elements «Remote
sensing»
|
Identification |
Designation informational requirement
|
|
|
To give attribute, labeling
environmental region situation on present-day moment with indication variations from
standard. |
|
|
To give information about
meteorological region situation with indication of cloudiness, humidity, transparency characteristics. |
|
|
To give cartographical data
of the surface territory observation, where practical fossil are conducted. |
|
|
To collect information about
meteorological situation on winning practical designs objects. |
|
|
To collect information about
status of mineral wealth design with indication of course squares troubles
mineral wealth. |
|
|
To collect information about
state of emergencies (SE) of the natural and man-caused character in a region
on the present situation. |
|
|
To give information about
amazed territories with environmental security troubles on the regions on the
present situation. |
|
|
To give information about SE
and man-caused character catastrophes on the present situation with
indication geographical location. |
|
|
To give the troubles of the
environmental security (toxin emissions, wood fires, oil spill, water body
shoaling and etc.) all over the republic territory. |
|
|
To give living population in
the stations, exposing to natural catastrophe (earthquake, pest insect invasion and so on) on the
territory of concrete region with territory of coverage refinement and periodic
time. |
|
|
To give information on SE of
natural character, taking place near concrete populated built-up areas in â prescribed temporal period. |
Table 2. List of informational previewing elements «Remote
sensing»
|
Code IE |
Title IE |
Code IE |
Title IE |
|
d1 |
Region |
d23 |
State of emergency (SE) of the man-caused nature (MCN) |
|
d2 |
Region title |
d24 |
Title of SE MCN |
|
d3 |
Code region
|
d25 |
Level code of SE MCN |
|
d4 |
Current ecological
situation |
d26 |
SE of the natural character |
|
d5 |
Date, time |
d27 |
Title of SE of the natural character |
|
d6 |
Attribute ecological situation index |
d28 |
Clump code of SE of the natural character |
|
d7 |
Violation ecological security index |
d29 |
Risk grade |
|
d8 |
Name index |
d30 |
Scope territory |
|
d9 |
Percent difference
tetrahedral standard |
d31 |
Object floor area |
|
d10 |
Meteorological situation |
d32 |
Object amazed square |
|
d 11 |
Cloudiness state |
d33 |
Geographical situation |
|
d12 |
Transparency state |
d34 |
Geographic latitude |
|
d13 |
Humidity state |
d35 |
Longitude |
|
d14 |
Mineral product (MP) |
d36 |
Built-up area |
|
d15 |
Array code MP |
d37 |
Built-up area name |
|
d16 |
Name MP |
d38 |
population, living in a built-up area |
|
d17 |
Meteorological situation on the crop and refinement MP objects |
d39 |
Title of a neighboring administration of a fast response on SE |
|
d18 |
Proprietor type of the crop object MP |
d40 |
Telephone of the attorney on SE |
|
d19 |
Name crop object MP |
d41 |
Tighten force amount of a fast response near a built-up area |
|
d20 |
MP indices |
d42 |
People amount for mobilization in a built-up area |
|
d21 |
Plan course square |
d43 |
Title of contiguous area |
|
d22 |
Real course square |
d44 |
Amazed square of contiguous area |
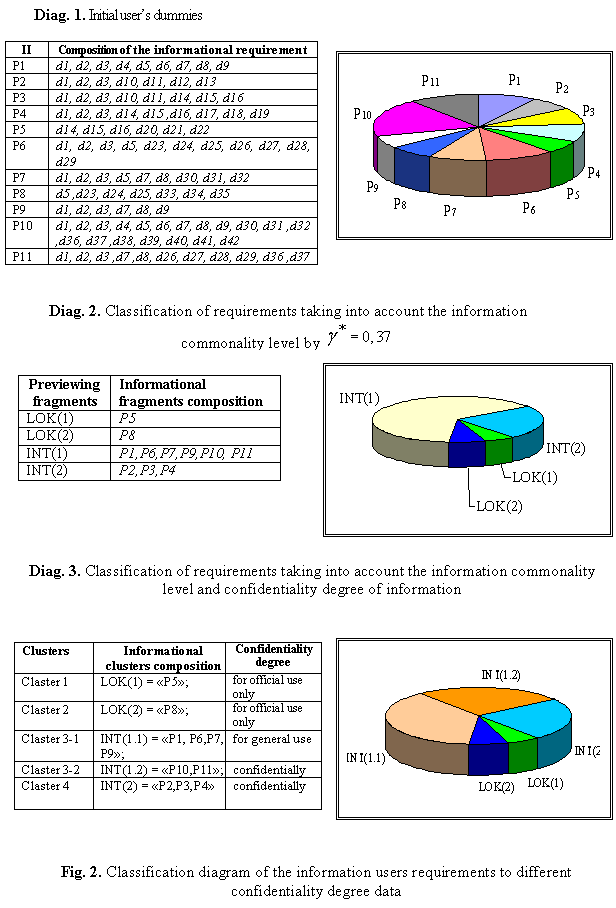
Local clusters contain user
requirements, which are independent of other information. Each integrated
cluster includes information requirements, among which the level of community
more than the given critical level.
For each cluster is calculating the integrated index of IE security
degree applying security matrix ![]() :
:
![]() ;
;
![]()
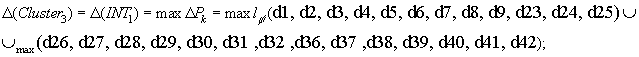
![]() As the analyses result Cluster3 is fractured on Cluster3-1and Cluster3-2 (Diagram
3):
As the analyses result Cluster3 is fractured on Cluster3-1and Cluster3-2 (Diagram
3):
Cluster3-1 = INT(1.1) =«P1, P6, P7, P9»; Cluster3-2 =
INT(1.2) =«P10, P11».
In the structural set IE is isolated the group IE (Table.3): ![]() . For all group elements, which may contain confidential information
it is necessary to determine the access rules, because they will be subject to
protection. There are several security objects (SO) (Table 4).
. For all group elements, which may contain confidential information
it is necessary to determine the access rules, because they will be subject to
protection. There are several security objects (SO) (Table 4).
Table 3. Subset
of group structural informational elements (IE)
|
GIE |
Name of group IE |
d1
|
Region |
|
d4 |
Present-day situation |
|
d7 |
Indicator of environmental
security disturbance |
|
d10 |
Meteorological situation |
|
d14 |
Mineral products (MP) |
|
d17 |
Meteorological situation on íà objects crop and refinement
(MP) |
|
d20 |
MP indices |
|
d23 |
State of emergency (SE) of a man-caused nature |
|
d26 |
State of emergency of a naturally character |
|
d30 |
Territory of a scope |
|
d33 |
Geographical location |
|
d36 |
Built-up area |
Table 4.
Set of security objects (SO)
|
Description SÎ |
Name SÎ |
Classification parameters of security objects |
||
|
Discipline type |
Status of primary presentation |
Attribute of simultaneity
reference to information |
||
|
Î1 |
Remote sensing |
Directoire |
Compound representation |
Library ‑ passive component |
|
Î2 |
Information about
meteorological situation |
File |
Secondary representation |
Document ‑
passive component |
|
Î3 |
Information about present-day environmental
situation |
File |
Compound |
Document ‑
passive component |
|
Î4 |
Information
about state MP |
File |
Original representation |
Document ‑
passive component |
|
Î5 |
Information about environmental
security disturbance |
File |
Original representation |
Document ‑
passive component |
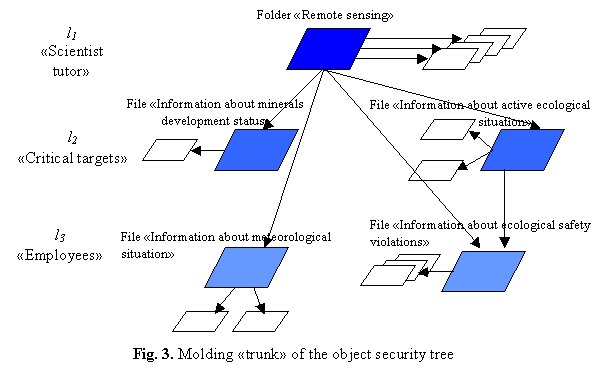
Tree
structure representation of objects of protection is implemented through a
hierarchy of rights of ownership of objects and subjects and the status of the
subjects in the administrative and management structure (Figure 3). A
classification of all selected elements of group for each local and integrated
segment is effected ![]() . Then for all objects of protection
. Then for all objects of protection ![]() , which are the main directories on the
"trunk", are defined the group elements with a value type object
"document" or "program".
, which are the main directories on the
"trunk", are defined the group elements with a value type object
"document" or "program".
Each
object of protection type "directory" is placed in the functional
dependence of the list of other types of objects of protection. This takes into
account [9]:
-specific
object of protection is only a passive component (![]() = "0"), or may be both passive and active
components (
= "0"), or may be both passive and active
components (![]() = "1");
= "1");
- a
status of specific object of protection is the primary carrier of information (![]() = "1"), or generated by the storage medium (
= "1"), or generated by the storage medium (![]() = "2"), or a secondary storage medium (
= "2"), or a secondary storage medium (![]() = "3");
= "3");
- a
type of specific object ![]() may be a
director, document, program, message.
may be a
director, document, program, message.
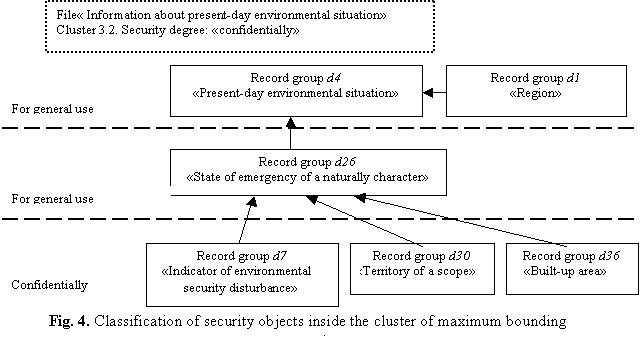
Tree «branches» of security objects
are presented on the Figure 4.
4. Conclusion
4. Conclusion
Suggested hierarchical
structure, mathematical models and computing procedures of security objects
classification with mandatory access to informational resources allows to solve
real-world problems. They were allowed to shape the tree-type structure of
minimally bounding clusters of informational requests of users with subject to
confidence of information. The tree structure of protection objects gives the
best picture of the access control, because take into account the features of
procedures with limited information use.
REFERENCES:
|
1 |
Scheglov A.Yu.
Security of the computer information from the unauthorized access. St.
Petersburg: Science and Technique, 2004. 384 p. (rus.) |
|
|
2 |
Leonard J
LaPadula and D. Elliott Bell “Secure Computer Systems: A Mathematical Model”,
MITRE Corporation Technical Report 2547, Volume II, 31 May 1973. |
|
|
3 |
Sokolova S.P.,
Gorkovenko E.V. Protection of access rights in the system with mandate policy
of information security. SPIIRAS Proceedings, issue 7, Editor – R.M. Yusupov,
Corr. Member of the RAS. St. Petersburg: Nauka, 2008. ‑ PP. 143 – 151.
(rus.) |
|
|
4 |
Gorkovenko E. V.
Multilevel security data base as the fundamental element of security information
technique of the different security degree //Proceeding ÕIV International
conference «Complex information security - 2009». Minsk: RBJ, 2009, (rus.). |
|
|
5 |
Gorkovenko E. V.
Management of data base and computing nets. //Science issue, Almaty: «Fylyì», 2005, pp. 56 ‑ 80. (rus.) |
|
|
6 |
Sokolova S.P., Gorkovenko
E.V. Intelligent monitoring subsystem of information security with mandatory
access control. Thesis of the Seventh Winter Symposium on Chemometrics
"Modern Methods of Data Analysis". St. Petersburg, 2010. PP.77 ‑
78, http://www.wsc.chemometrics.ru/wsc7. |
|
|
7 |
Tarakanov A.O., Skormin V.A., Sokolova S.P. Immunocomputing: Principles
and Applications., N.Y.: Springer. 2003. 193 ð. |
|
|
8 |
Sokolova S.P. and
etc. Intelligent analysis of multilevel data by immunocomputing. Almaty:
IPIC, 2006, 110 p. (rus.) |
|
|
9 |
Basan A.S. Security object
classification by supporting of mandated access differentiation in SCBD //
Proceeding of VIII International science-practical conference
"Informational security". Taganrog: TRTU, 2006. PP.128 ‑ 130.
(rus.) |
|
|
10 |
Tishkov A.V.,
Kotenko I.V., Sidil’nokov E.V., Chervatjuk O.V. Detection and resolution of
conflicts in security policies. //Proceeding of the second international
conference on problems of security and counter terrorism. M.: MCSMS, 2006.
PP. 172 ‑ 185. |
|
|
11 |
Stepashkin M.V.,
Kotenko I.V., Bogdanov V.S. Intelligent system of vulnerability analysis of
computer networks. // Proceeding of X national conference on the artificial
intelligent. V. 1. M.: Fizmatlit., 2006. PP. 149 ‑ 157. |
|
|
12 |
Kulba V.V.,
Kovalevskiy S.S., Kosiachenko S.À., Sirotjuk V.O.
Theoretical bases of the optimal architecture designing of distributed data
base. M.: IPC RAS, 1999. PP.107-113. (rus.) |
|
|
13 |
Gorkovenko E. V.
Informational security administration in the corporate net of the cosmic infrastructure.//Bulletin
of national engineering academy of the Republic Kazakhstan, ¹1 (23) Almaty:
2007, PP. 60 ‑ 65. (rus.) |
|
|
14 |
Gorkovenko E. V.
The generation of subjects and objects security nets for multilevel model of
access differentiation //KazNU Bulletin,
¹ 3(50), Almaty: 2006. PP. 104 ‑ 110. (rus.) |
|
|
15 |
Gorkovenko E. V.
Securing thematic information resources on the corporate network infrastructure
space. //Proceedings of ÕII International science-practical conference «Reshetnevskiya chteniya». Krasnoyarsk: SSAI, 2008. PP. 396 ‑ 399. (rus.) |
|
|
16 |
Gorkovenko E. V.
Multilevel access control in corporate networks of space infrastructure.
//Mathematical magazine, V. 7, ¹3 (25). Almaty: IM MES RK, 2007. PP. 28 ‑
34. (rus.) |
|