Современные
информационные технологии/4. Информационная
безопасность.
Karlygash Mukhitova
International University Information Technology
Almaty, Kazakhstan
The
importance of Information Risk Management in developing risk management
capability of organisations
Abstract
Due the improvement of the information
technology, the importance of information has heightened enormously. All
valuable assets of enterprises are based on information. From this point, every
organisation has started to focus on managing risks of information leakage. Managing
information risk is essential and problematic. However, the representation of
the Risk Management has enabled different approaches for controlling assets of
companies. This article discusses Information Risk Management techniques and
discusses how standards and policies are important to protect information and
other enterprise assets. In
addition, this paper shows the importance of Information Risk Management for
organisation.
1. Introduction
Risk has been identified
one of the integral part in economy and policy, which has valuable impact on
the development of an organisation. Risk identification helps to the
organisations to avoid future challenges, furthermore, to manage and evaluate
all possible risks. Hopkin and Paul (2013) defined risk as an economical
and financial phenomenon, which have a negative impact on organisations and
companies. Accordingly, most of the enterprises have been attempting to
minimize risk, which caused appearance of the term Risk Management (RM).
Managing risks are
directly related to efficiency and timeliness decision of the problems. RM is
an important component in developing organisation and enterprise structure.
Over the past century, there has been a great attention on risk management structure.
Kenneth et al (1993) found that financial executives considered risk management
as the main issue and it has been taking a great attention from researchers in
finance. In general, RM is about attempting to find best possible solution for problems by preventing from negative
outcomes and minimizing the damage. Another importance of RM within
organisation that diminishing more likelihood outcomes. In general, RM has
enormous impact on organisations and enterprises; it helps to become successful
and to have a defined strategy and tactics to reduce several issues by deeply
organising threats (ibid). For these reasons, RM has been an obligation for
several companies, however, for some regulated sectors, it is not appropriate
choice. Telecommunication, banking, oil industry and insurance, all of them are
example of regulated sectors, which are followed by some identified structure
and tendency (Gupta 2012). Hence, in RM exists processes that characterized as
the process frameworks. Enterprise Risk Management one of the main frameworks
of RM (Lam 2014). It is responsible to set frameworks, policies, methods and
standards and provides risk monitoring (ibid). There has been several methods
and standards of the Enterprise Risk Management. The author of this paper is
more focused on Information Risk Management, which is recognised as the
component of the Enterprise Risk Management. There has been several reasons to
choose Information Risk Management:
-
The
strategy and technics of organisation are based on the information;
-
It has
been assumed that most companies suffering from information leakage,
consequently, taking into account security of information might be significant
for them;
-
Identifying
and preventing security of the information is valuable, in order to have good
strategy considering the level of competitiveness of each organisation;
-
All of
the codes and guides are information based; it proves the necessity of the
information protection.
The major objective of
this paper is to show importance of the Information Risk Management and to
indicate several principles of Information Risk Management to develop
organisations’ risk management capability.
2. Understanding Enterprise Risk Management
As it was mentioned above,
Enterprise Risk Management is strategies and methods to manage and manipulate
companies and organisations (Lam 2014). It also provides guide to companies: to
improve plans and enhance company’s strategy, to determine gaps in the existing
practices and to find ways to strengthen them (ibid).
Enterprise Risk Management is
applied in strategy setting, intended to define potential risks, which might
occur and can effect to the business structure. Furthermore, it shows how to
manage risks and provide “reasonable
assurance regarding the achievement of entity objectives” (Moeller, 2007).
Companies which accepted
Enterprise Risk Management have improvements on developing business strategies
and achievements overall. Moreover, by adopting Enterprise Risk Management
framework can lead to reduced losses, enlargement earnings (Lam 2014).
3. The Importance of Information Risk Management
in organisations
Having clearly identified data and information the
organization can create a proper strategy and tactics in order to develop risk
management. The importance of information have heightened due to the confidentiality and competition among organisations.
Information Risk Management considers one of the main aspect and developing
directions in the risk management area.
The risk in
Information Risk Management context is the possible threat that will may exploit system vulnerability and destruction on
information confidentiality and integrity (Carrol 1996), whereas, vulnerability
defines as “a weakness, holes, flaws which can be exploited by threat and cause
damages in the whole organisation” (Stephenson 2004). Taking into consideration
given descriptions, it might to be concluded that risks to information can be
resulted from “modification, disclosure, destruction”. In order to solve this
issue enterprises should accept Information Risk Management to estimate and
assess risks on information (Hong et al. 2002).
Before
understanding the whole structure of Information Risk Management, it is
important to understand what the word information covers. Information is considered
as a data, which is organized in a significant context (Sutton 2014). Due to
the recent developments in information technologies and increasing number of
hacking attacks have heightened the value and security of the information. The
whole structure and strategy of the business and organisations are based on
information, consequently, managing information risks are defined significant
approach in developing and improving business approaches (ibid). The following
figure shows the information’s lifecycle phase.
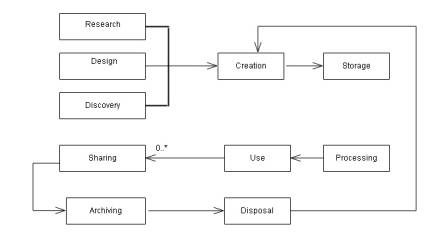
Figure
1. The Information Lifecycle (Sutton 2014)
The
given figure describes, the process of information; every stage of the
lifecycle requires the information to be protected, hence, it has been seen
that the need of information risk management are compulsory (Sutton 2014).
According
to Sutton (2014) any organisation have at least piece of information, which has
enormous value to the organisation, hence, the Information Risk Management are
needful for them. For example, taking into account departments of the
organisation, Finance department mostly save stores information about profits
and expenditure; IT department attempts to keep it more secure, whereas, Human
Resources hold records about personal information. All these information are
significant for companies and must be protected in order to avoid the
information leakage. As Sutton (2014) described in his book, information risk
is a part of the business risk, which is strongly linked with “confidentiality,
integrity and availability of business information assets”.
He
pointed out three basic information principles:
-
Confidentiality (those people who have access can view it);
-
Integrity (those people who have access can modify
information);
-
Availability (information should be available for authorised
people, when they want to have access).
Taking
into consideration these properties of information, it can be clearly seen that
information is the most valuable aspect of the organisation. Protection from
unauthorised access (modification, information loss) might influence to the
development of organisation.
Sutton
(2014) have classified the following risks, which might be resulted in
information risk:
Š
Financial loss;
Š
Defect on organisation operations;
Š
Reputational damage;
Š
Legal and regulatory penalties
As
can be clearly seen from previews sections, risk is incidental in companies and
enterprises and failures can cause disasters to the organisation. In addition,
information is critical, moreover, damage on information can cause severe
consequences on developing organisation. Revising all mentioned above,
Information Risk Management is crucial for the organisations and Sutton in his
book Information Risk Management: A
Practitioner’s Guide examined of the necessity of Information Risk Management
to business strategies. In addition, some benefits from understanding
information risk:
1. Organisation
more likely to have advantages on managing (reducing future risks) comparing
with competitors, which do not follow information risk management;
2. If
unsuspected situations occur, they might have diminished level of impact and
loss;
3. If there is
unexpected events, organisation can recover more quickly and efficiently;
4. Reducing
number of risks and future consequences;
5. Improved
organisation structure (Sutton, 2014).
4. Information Risk Management Structure
Information
security and protection is a crucial to the organisation, accordingly, the
importance of information have been estimating. The best approach of
information prevention is to take Information Risk Management as the main
component of their company and it more likely helps to prevent any negative
outcomes (Pironti 2008). Number of researchers found that processes, procedures
and policies provide effective defence on information rather different software
tools. A large amount of attacks have been committing, hence, this can prove
that technological control framework might not be appropriate to protect
information infrastructure. There has been a view that implementing new
policies and standards could be efficient way of information security. Pironti
(2008) identified Information Risk Management one of the basic areas of
organisation’s information infrastructure that examines information should be
protected and determines the level of protection. Moreover, Information Risk
Management classifies the value of information and impact on organisation’s
business strategy.
According
to ISO/IEC Standard Information Risk Management has two approaches: directed on
achievement confidentiality and supporting the level of confidentiality,
integrity and availability (Humphreys 2006). Information Risk Management covers next in information
security aspects:
-
Realization, planning and monitoring of information
security;
-
Provision information security requirements and principles;
-
Provision any hazardous circumstances by the standard and
strategy of risk management;
-
Assurance of personal and staff education relating to
information risks and security;
-
Auditing and rechecking of concepts and security issues (Wheeler 2011)
Sutton
(2014) offered process of information risk management, which consists four key
levels:
1. Identification
and qualification of the risk;
2. Decision-making
process (related to identified risks in the level 1);
3. Applying the
appropriate controls in order to reach the objectives, which is defined in the
level 2;
4. Acceptance of
any risks, which might be found after implementation level 3.
In
addition, Landess (2003) suggested the following steps of Information Risk
Management process:
1. Risk
identification- defining the event, which might occur. This step involves
revealing threats, vulnerabilities of the system;
2. Risk
analysis- assessment and measure of threats and vulnerabilities by
sophistication level and in order to choose appropriate information security
control.
3. Controlling-
using methods, policies and procedures to manage current risk;
4. Monitoring –
evaluation of the risks;
5. Report- final
step, which includes decision making process.
In Information Risk Management during risk identification
process the following approaches has done in order to find possible risks:
-
Threat analysis;
-
Vulnerability assessment;
-
Penetration Testing;
-
Auditing (external and internal);
Risk
analysis includes risk assessment, where plans and ideas for information
security are offered in order to
implement any suggestions and solutions. It also analyses deeply any possible
threats and attempts to find the consequences of that issue before identifying
what should be done (Hopkin 2013). During risk assessment organisation examines
threat and vulnerabilities of the information system. After risk assessment
organisation must make decision on risk treatment about prevention, reducing
and acceptance of the threat (Wheeler 2011). Risk communication “requires
organisation setting roles, communication procedures and roles for managing
risks, it also reviews risk action plans” (Hopkin, 2013). In addition, risk management involves
risk communication, which considers collection of information in order to
identify and classify risks, hindering failure of information security,
reducing risk outcomes, and it includes monitoring and reviewing of the risks
(ibid).
5. Conclusion
Returning
to the main question of the current article, it is now possible to state that
Information Risk Management has significant impact on developing organisation.
Importance of Information Risk Management has considered due to fact that every
organisation has at least piece information. Moreover, that information can be
key structure of business plan or strategy. However, some enterprises do not
pay more attention on information risks. If they have some comprehension of
information risk, in the most cases companies buy software tools in order to
check information security. One of the significant finding showed that
procedures and strategies could be more beneficial rather than different
programs and applications. Taking into consideration this statement, it might
be established that information risk managements should be implemented in each
organisations and companies. In addition, considering the structure of
Information Risk Management, this essay helped to extend understanding
information risk management processes and identified each steps.
6. Reference List
Culp, C. (2001)The Risk Management
Process: Business Strategy and Tactics. 1st edn. United States: Wiley, John
& Sons, Incorporated.
FROOT, K., SCHARFSTEIN, D. and STEIN, J. (1993) ‘Risk Management: Coordinating
Corporate Investment and Financing Policies’,The Journal of Finance,
48(5), pp. 1629–1658. doi: 10.1111/j.1540-6261.1993.tb05123.x.
Gupta, A. (2012)Risk management and simulation. United States: Taylor
& Francis.
Hopkin, P. (2013)Risk Management. United Kingdom: Kogan Page Ltd.
Humphreys, T. (2006) ‘State-of-the-art information security management systems
with ISO/IEC 27001:2005’,ISO Management Systems.
Lam, J. (2014)Enterprise Risk Management: From Incentives to Controls.
United States: Wiley.
Landess, D. (2003) ‘A Practical Information Risk Management Process Framework’,GIAC
Security Essentials.
Moeller, R. (2007)COSO Enterprise Risk Management: Understanding the New
Integrated ENTERPRISE RISK MANAGEMENT Framework. United States: Wiley, John
& Sons, Incorporated.
Pironti, J. (2008) ‘Key Elements of an Information Risk Management Program:
Transforming Information Security Into Information Risk Management’,I N F O
R M AT I O N S Y S T E M S C O N T R O L J O U R N A L, 2.
Sutton, D. (2014)Information Risk Management: A Practitioner’s Guide.
United Kingdom: BCS Learning & Development Limited.
Ward, S. (2005)Risk Management Organisation and Content. 1st edn. 32-36
Aylesbury Street: Witherbys.
Wheeler, E. (2011)Security Risk Management: Building an Information Security
Risk Management Program from the Ground Up. Waltham, MA: Elsevier Science.